Alfresco & CAS SSO
Alfresco supports the standard use of CAS for single-sign on for its web user applications, ie /share and /alfresco via the External authentication subsystem. However Webdav must be configured for CAS using apache mod_auth_cas. This blog provides details on how to setup Alfresco for CAS using jasig client and mod_auth_cas for webdav.
Alfresco and Jasig CAS server Setup
The Alfresco ECM webapps, (/share and /alfresco) can be configured to support single sign-on using the Central Authentication Service (CAS). The purpose of CAS is to permit a user to access multiple web applications while providing their credentials (such as userid and password) only once. Following an initial user login, CAS also allows web applications to authenticate users without gaining access to a user’s security credentials, such as a password.
As shown in the diagram below, CAS involves at least three parties: a client web browser, the web application requesting authentication, and the CAS server. It may also involve a back-end service to manage user credentials or connect to an LDAP server.
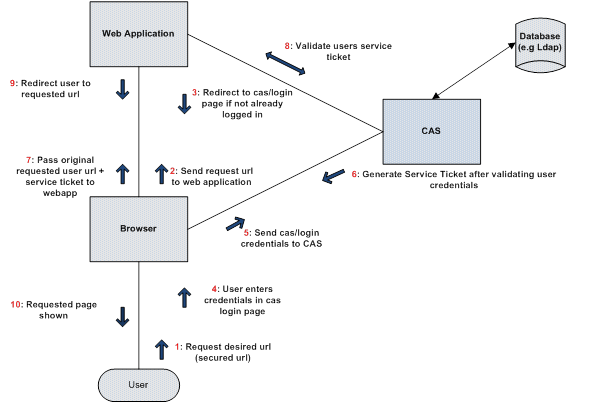
When the client visits an application and is not already authenticated, the application redirects it to CAS and CAS presents the user with a login form. The user provides their login credentials and CAS validates the client’s authenticity, usually by checking a username and password against a database (such as Kerberos or Active Directory).
If the authentication succeeds, CAS stores a service ticket (TGT) as a cookie on the user’s browser and then CAS returns the client to the application url originally requested. The application then validates the ticket by contacting CAS over a secure connection and providing its own service identifier and the ticket. CAS then gives the application trusted information about whether a particular user has successfully authenticated.
(Note: the security ticket (TGT) is passed with all subsequent application requests for SSO against CAS)
Alfresco-CAS_Client Setup
Once we have a running CAS server, alfresco can be configured to use the Jasig Java CAS client to connect to the CAS server.
In order to make the CAS authentication and validation filters available to Alfresco, the cas-client-core-3.x.x.jar(Available from http://downloads.jasig.org/cas-clients/ ) file needs to be added to the lib directory of each webapp (both share and explorer).
The next step is to declare and then apply the CAS client authentication and validation filters. Hence the following lines have to be added to web.xml for alfresco share and explorer.
Declaring the filters
<filter>
<filter-name>CAS Authentication Filter</filter-name>
<filter-class>org.jasig.cas.client.authentication.AuthenticationFilter</filter-class>
<init-param>
<param-name>casServerLoginUrl</param-name>
<param-value>https://<CAShost>/cas/login</param-value>
</init-param>
<init-param>
<param-name>serverName</param-name>
<param-value>http://<SERVERhost></param-value>
</init-param>
</filter>
<filter>
<filter-name>CAS Validation Filter</filter-name>
<filter-class>org.jasig.cas.client.validation.Cas10TicketValidationFilter</filter-class>
<init-param>
<param-name>casServerUrlPrefix</param-name>
<param-value> https://<CAShost> /cas</param-value>
</init-param>
<init-param>
<param-name>serverName</param-name>
<param-value> http://<SERVERhost> </param-value>
</init-param>
</filter>
<filter>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<filter-class>org.jasig.cas.client.util.HttpServletRequestWrapperFilter</filter-class>
</filter>
Applying the filters
For Alfresco Share
<filter-mapping>
<filter-name>CAS Authentication Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter-mapping>
<filter-name>CAS Validation Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter-mapping>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
For Alfresco Explorer
<filter-mapping>
<filter-name>CAS Authentication Filter</filter-name>
<url-pattern>/faces/*</url-pattern>
</filter-mapping>
<filter-mapping>
<filter-name>CAS Validation Filter</filter-name>
<url-pattern>/faces/*</url-pattern>
</filter-mapping>
<filter-mapping>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<url-pattern>/faces/*</url-pattern>
</filter-mapping>
Activating SSO for Alfresco Share
In order to activate SSO, alfresco share needs to be enabled so that a header and cookie-based authentication connector is used and this is done by adding the following entry in share-config-custom.xml (available from share-config-custom.xml.sample).
<config evaluator=”string-compare” condition=”Remote”>
<remote>
<connector>
<id>alfrescoHeader</id>
<name>Alfresco Connector</name>
<description>Connects to an Alfresco instance using header and cookie-based authentication</description>
<class>org.alfresco.web.site.servlet.SlingshotAlfrescoConnector</class>
<userHeader>SsoUserHeader</userHeader>
</connector>
<endpoint>
<id>alfresco</id>
<name>Alfresco – user access</name>
<description>Access to Alfresco Repository WebScripts that require userauthentication</description>
<connector-id>alfrescoHeader</connector-id>
<endpoint-url>http:// <ServerHost>/alfresco/wcs</endpoint-url>
<identity>user</identity>
<external-auth>true</external-auth>
</endpoint></remote>
</config>
Adding the External Authentication subsystem to the Authentication chain
For Alfresco to be able to use an external authentication mechanism, the External Authentication subsystem must be enabled to use the header and also added to the Alfresco Authentication chain. So the following entries were added to alfresco-global.properties.
authentication.chain=external1:external
external.authentication.proxyUserName=
external.authentication.proxyHeader=SsoUserHeader
external.authentication.enabled=true
external.authentication.userIdPattern=
Customising Alfresco Share Logout Controller
The Alfresco share logout controller had to be overridden so that users could log out of Alfresco and CAS.The customised logout controller was packaged in logoutCAS.jar and copied to share webapp lib directory. Then the bean definition referencing the modified logout controller was added to $ALFRESCO_Home/tomcat/shared/classes/alfresco/web-extension/custom-slingshot-application-context.xml.
<bean id=”logoutController” class=”org.wwarn.cms.authentication.servlet.CASSlingshotLogoutController”>
<property name=”cacheSeconds” value=”-1″ />
<property name=”useExpiresHeader”><value>true</value></property>
<property name=”useCacheControlHeader”><value>true</value></property>
<property name=”connectorService” ref=”connector.service” />
<property name=”casHost”><value>https://CAShost</value></property>
<property name=”casPath”><value>cas/logout</value></property>
</bean>
Note;
The share-config.xml file also needs to be modified
From
<item type=”link” id=”logout” condition=”!context.externalAuthentication”>/dologout</item>
To
<item type=”link” id=”logout”>/dologout</item>
Customising Alfresco Explorer Logout
The Alfresco Explorer logout has to be redirected so that users could log out of CAS and alfresco. This is achieved by editing the relogin.jsp file of the alfresco webappas follows;
if (authCookie != null)
{
authCookie.setMaxAge(0);
response.addCookie(authCookie);
}
}
// Logout from CAS
response.sendRedirect(“https:// CAShost /cas/logout”);
%>
Alfresco WebDAV and CAS SSO
Alfresco WebDAV allows users to view the alfresco repository in a folder like structure using http and can be a very handy feature to have. In setting this up we discovered that Alfresco Webdav is not supported using CAS Jasig client and the Alfresco External authentication subsystem. The main reason being that the “desktop DAV client does not respect the ‘302
Redirect’ necessary for authentication”.
Hence the solution is to use apache and the mod_auth_cas module to handle WebDAV. Mod_auth_cas is an Apache 2.0/2.2 compliant module that supports the CASv1 and CASv2 protocols. The following configuration instructs apache to explicitly use mod_auth_cas to authenticate users. This should be inserted into the apache .conf file
<Location /alfresco/webdav>
AuthType CAS
AuthName “CAS”
require valid-user
CASScope /alfresco
</Location>
Update the mod_auth_cas.conf file, setting the correct url for your cas server:
# The URL to the CAS server
CASLoginURL https://<yourCASserver>/cas/login
CASValidateURL https://<yourCASserver>/cas/serviceValidate
CASProxyValidateURL https://<yourCASserver>/cas/proxyValidate
Note:
This solution assumes that you have connected Apache and Tomcat using Mod_SSL and Mod_jk and that you have configured mod_auth_cas to authenticate against the CAS server.

